How to Enable/Disable the SSH for the ESXi
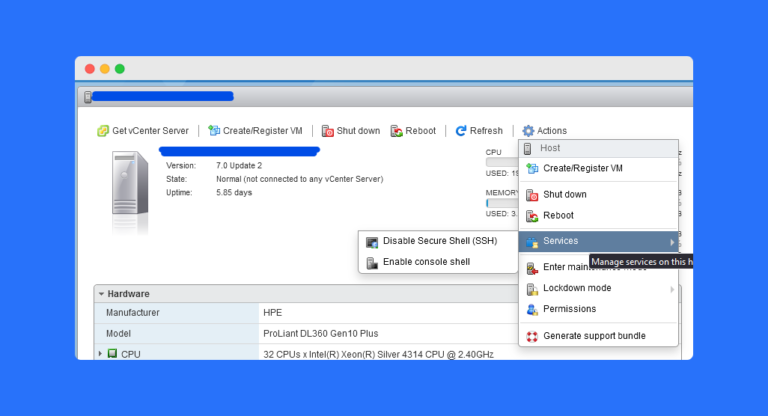
In day to day task we used ssh for connecting to your ESXi host. There are lots of customer who block the ssh service due to security concern. So when ever we need to troubleshoot those host we need to…

In day to day task we used ssh for connecting to your ESXi host. There are lots of customer who block the ssh service due to security concern. So when ever we need to troubleshoot those host we need to…

Having an Internet monitoring setup is so important. For home, it is not that important but for big organizations and data centers, it is so critical. In this post, I will talk about my internet monitoring setup. How I did…

How to Change the Timezone on Linux. Proper time and timezone play an important role in Linux. It is easy to check time in your geo format. If you have the proper time and timezone. It will help you in…
From the previous article, we already saw how to set up a dedicated Docker Host In VirtualBox. Now this article will see how we can install the Portainer. Also will see why we need to use the Portainer. What is…

SSH is one of the most common methods of connecting to the host. The default root user is usually used to log on to the server when we deploy it. When we tried that we encountered the message that you…
In today’s article, we won’t talk about much. This is a simple docker installation article. You just need to throw these commands in your Linux terminal and you are good to go. Your docker will be installed. Let’s see how…
Ads are becoming the new homepage of the internet. Almost every website on the internet is trying hard to sell us ads. Is there any solution using which we can stop those annoying ads? Today’s article will discuss that only.…

With the new generation, things are more online. From food to experience everything is online now a day. We store most of your documents and images online due to their ease. But due to an increase in the demand for…
With the increased amount of privacy concerns, the checksum plays an important role. To make sure the file are temper proof. This article will discuss the checksum and how we can use the checksum to secure our files. What is…
Follow the below steps to have a static IP Static IP Address Assignment 1.) Login to the ubuntu server 2.) After that enter the below command to edit the network file 3.) Add the below code in the file, Please…